Proxmox Networking for VMware People
I’ve been making the move from VMware vSphere to Proxmox as part of a 2024 New Year resolution, and this has led to a lot of silly questions as Proxmox’s networking can best be described as “similar, but different”.
This post will cover how to replicate common vSphere networking setups in Proxmox. Please note, I’ll only cover Linux networking, not OVS or the newish SDN feature in Proxmox.
Why do I have to “Apply Configuration”?
Proxmox is fundamentally based on Debian Linux whose networking is built upon the ifupdown package. Proxmox builds on this by using ifupdown2, an improved version that makes life easier for developers, but the fundamentals for end users are the same.
When a configuration change is made, you’re editing /etc/network/interfaces to include the new configuration. Proxmox won’t apply the changes straight away as you may be making multiple changes which are dependant on each other and reloading the configuration does have the potential to briefly disrupt the network.
Creating vSwitches in Proxmox
Proxmox’s Linux networking can act like a standard vSwitch within vSphere, but the terminology is a little different. Of the options presented, the one you’re interested in is “Linux Bridge”.
Once you click this, you’ll be presented with this.
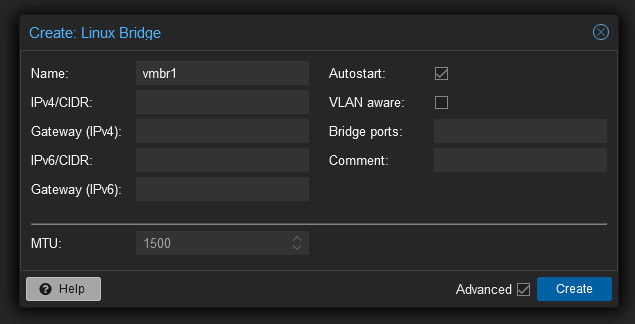
This is one aspect of Proxmox you’ll have to get used to: Endless forms with not a lot of hints, though the Help button generally works well.
Here are the options relevant for vSwitches
VLAN Aware
This allows the bridge to pass around dot1q tagged traffic. If you leave this unchecked, it is still possible to use VLANs on a guest’s NIC, but Proxmox will create VLAN NICs bridged to your Linux bridge in the background to achieve this.
If you are using VLANs, I strongly recommend you enable VLAN awareness.
Bridge Ports
This is the equivalent of assigned physical adapters in VMware and is essentially what interfaces the bridge is actually connected to. Unlike VMware, this doesn’t need to be a real physical adapter. I’ll cover bridging to bonded interfaces in the link failover section.
IP Addresses?
One thing that may seem confusing is the form asks for IP networking configuration. This is because Linux bridges combine two separate VMware concepts, that of a VMkernel adapter and its associated network.
Configuring an IP address is optional, guests can still use the bridge without it.
Networking Within the Hypervisor Only
With vSphere, it’s possible to create a vSwitch with no physical ports that just passes traffic between connected guests. This is useful if you use a software router such as OPNsense to handle layer 3 routing, NAT, etc. for your guests as you won’t want to connect them to an outside network.
This is extremely simple with Proxmox. It’s literally as simple as leaving the “Bridge ports” field empty.
Link Failover Configuration
VMware vSphere standard switches have a direct relationship with the physical network adapters they’re assigned to (if any). In VMware, active-active, active-passive, etc. link failover is achieved by just setting the interface order for the vSwitch.
Proxmox approaches this a little differently, failover is achieved by creating a new interface called a Linux Bond. Below is an example configuration that mimics the active-passive configuration above.
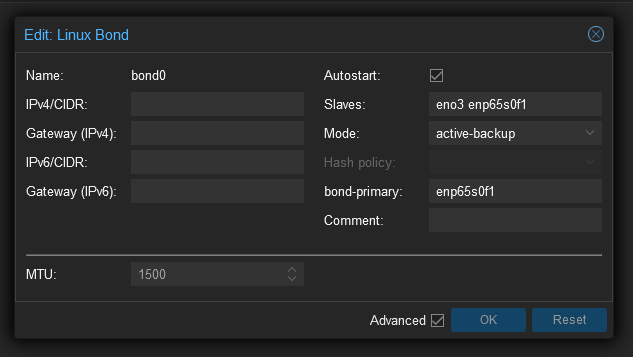
In this instance, eno3 and enp65s0f1 are actual physical network interfaces. As enp65s0f1 is the primary, it’ll always use that whenever a link is available and only use eno3 as a last resort.
As with bridges, IP address configuration is optional. You cannot plug a guest’s NIC directly into a bond, so an IP address configuration is likely only useful for creating a management interface that has link redundancy.
A Linux bridge may make use of a bonded interface by simply bridging to it. Specifying the Linux bond’s interface name as the bridged port is all you need to do.
Port Groups
In the VMware world, a port group is used for connecting guests to a vSwitch. It is intended to be analogous to a switchport on a real world network switch.
Proxmox approaches this a little differently, there are no port groups and the VLAN configuration is held by the guest’s NIC. This is akin to if you could attach a VMware guest directly to a vSwitch and just specify the VLAN directly on the guest interface.
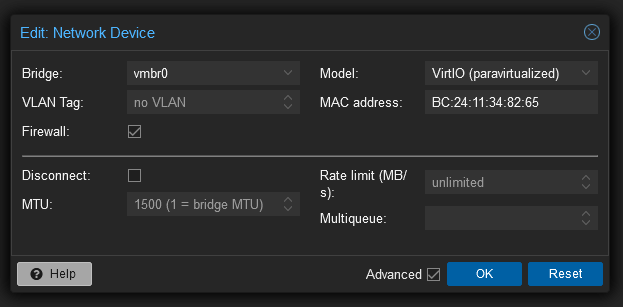
VLAN Tag
The VLAN Tag field is self-explanatory, guest traffic passing through the bridge will be tagged with the value you specify here. However the “no VLAN” placeholder when nothing is inserted is somewhat misleading, as in the case of a VLAN Aware bridge, it acts like a port group tagged 4095. It’ll pass all tagged and untagged traffic.
If you just want untagged traffic, you may “tag” the port as VLAN 1, which acts like the “None” option in VMware, and disables VLANing for the NIC.
VMkernel NICs on Specific VLANs
In vSphere, it’s possible to configure the management interface to sit on a specific VLAN by configuring a VLAN ID for the VMkernel NIC’s port group. Proxmox approaches this a little differently, since any interface is a candidate for carrying management traffic, we instead just create a Linux VLAN interface and configure an IP on it.
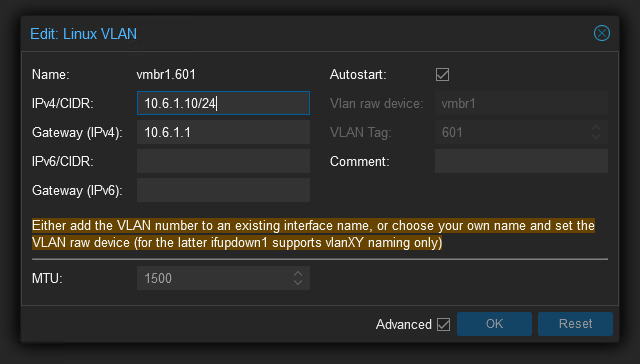
In this example, I’ve used a common naming convention of Device.VLAN, which Proxmox picks up on and auto fills to the correct device and tag. Any guest or physical network plugged into vmbr1 can reach Proxmox on VLAN 601 with this configuration, and no IP configuration is required on the bridge.